Web Application Security with IAM, WAAP and MFA
Protect web applications and APIs with Web Application Security
Web applications and APIs are points of access to company data and applications. Customers and employees can access information quickly and easily at any time from anywhere. Cybercriminals also use these gateways. Around 60% of all successful cyberattacks are the result of insufficiently protected web applications.
Your benefits
Requirements-based performance models (SaaS, dedicated servers)
Data storage and operation exclusively in Switzerland (ISO 27001)
Many years of expertise with a broad range of services and scalability
When is it the right solution?
Are you looking for a centrally controllable, highly available and secure solution to protect your ecosystem, including web applications and mobile solutions? Do you want your web application and API protection (WAAP) provider to offer a wide range of additional, modular cyberdefence solutions, such as Threat Detection & Response (TDR) or Secure Operations Center (SOC)?
Web Application Security from Swisscom gives you a cost-efficient, standardised solution that can be individually adapted to your requirements. Different models are available for operation.
Get started with Web Application Security
The first step
Let us introduce you to the world of Web Application Security and support and guide you with our expertise.
Downloads
Web Application Security factsheet
Web Application Security
Managed Security Services
Firewall, WAAP and IAM
- Web application firewall (WAF) and API protection plus a flexible IAM solution
- Advanced protection against OWASP’s Top 10 security risks based on real-time threat data
- Modular structure with encapsulated functions and add-ons such as single-sign-on (SSO) and geofencing
- ISO 27001-certified, Switzerland-based data centres with data storage also in Switzerland
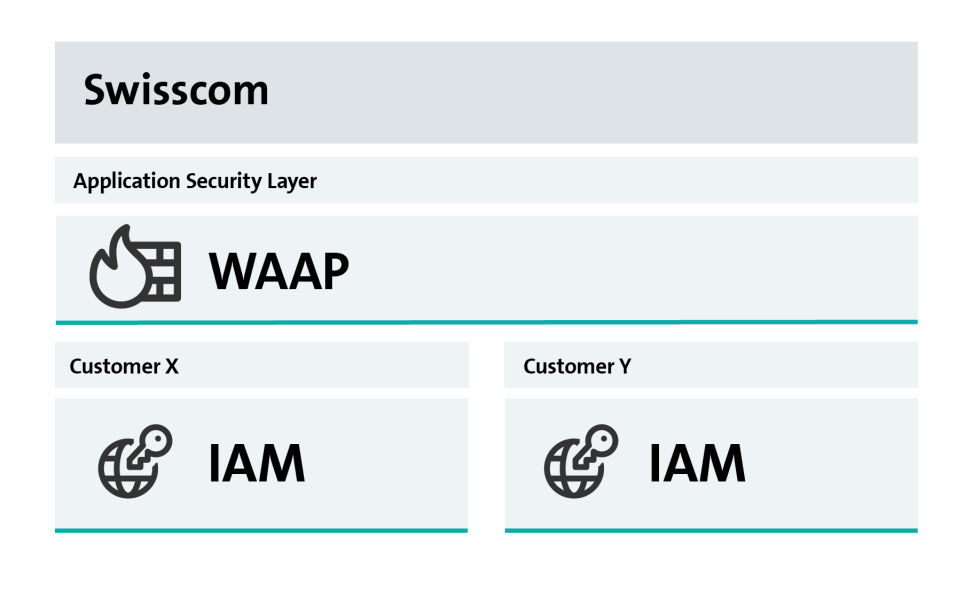
Dedicated environment
Highly secure and powerful
- Extensive customisation options due to the WAAP and IAM solution’s close alignment to customer needs
- Operation of Ergon Airlock and Nevis on classic virtual machines or using container technology
- ISO 27001-certified, Switzerland-based data centres with data storage also in Switzerland
- Operation of state-of-the-art WAAP and IAM solutions from leading Swiss manufacturers
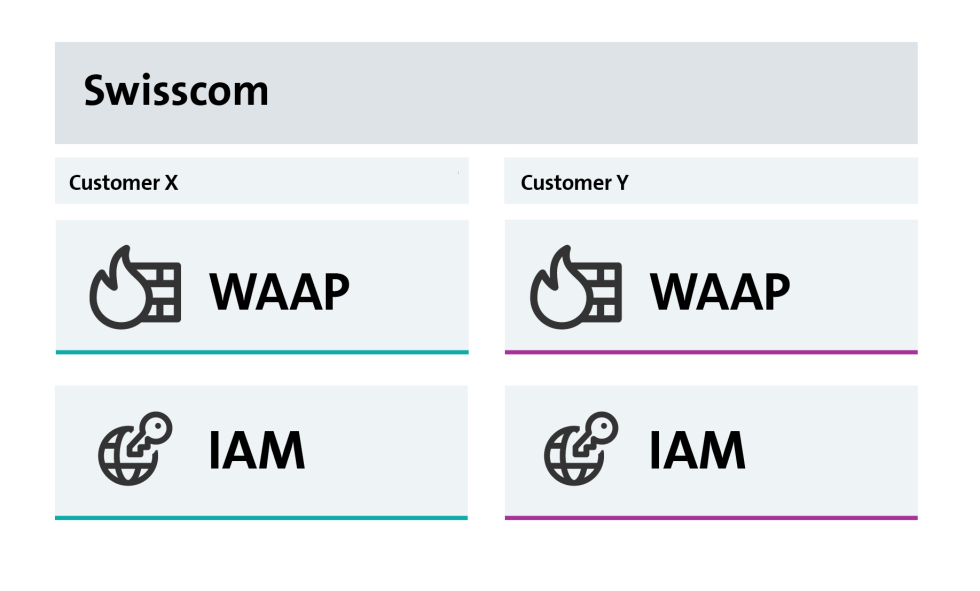
Advisory
Expert advice on web application protection, APIs and access control
- Personal security expert as your dedicated contact
- Setup or optimisation of WAAP/cIAM solutions based on Airlock
- Periodic or situational support to secure your web applications
- Joint design of your web architecture
- Review of existing solutions based on the Azure web application firewall (WAF) and Azure firewall
- Wide range of services and end-to-end support if required
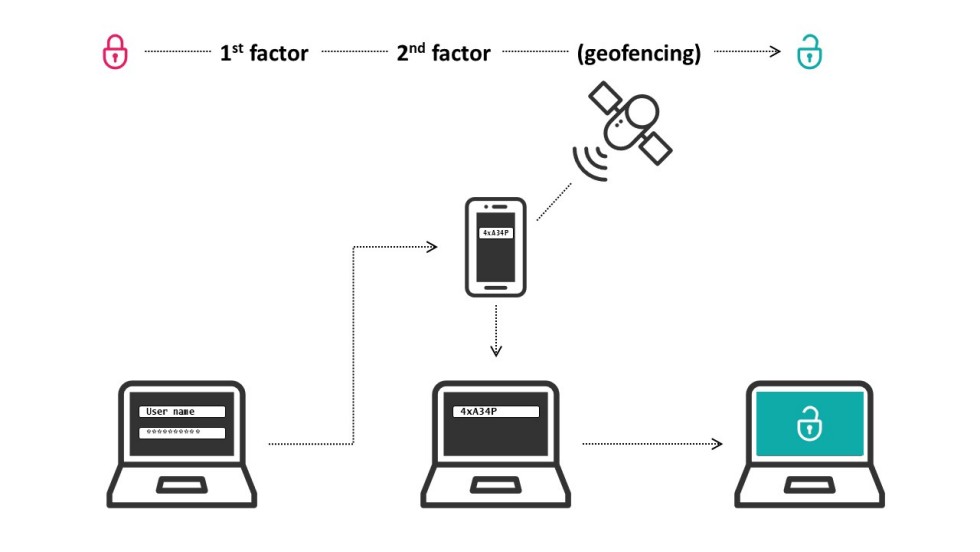
Multi-factor authentication (MFA)
Maximum authentication security
- A simple addition to existing login options, such as user name and password
- Different app-based login procedures and support with the distribution of hardware tokens
- Dynamic methods to protect against phishing and fatigue attacks
- Precise geofencing as an option for enforcing advanced policies and preventing bypassing via VPN
Additional information
Connectivity and open banking
Intelligent core banking systems are open to external innovations and increasingly rely on digital ecosystems.
Our platinum partnership
Ergon Informatik AG
Intelligent core banking systems are open to innovations from the outside and increasingly rely on digital ecosystems.
Secure corporate payment transactions
Drawing on many years of industry experience and in-depth expertise, we are an Airlock Platinum integration partner.
Do you have any questions regarding Web Application Security? Get in touch.






