Extended Detection and Response
Extended Detection and Response (XDR) – for reliable protection of the IT infrastructure
70 percent of all successful cyber attacks start on an endpoint.
Preventative protective measures, such as anti-virus software, are therefore not enough on their own. Extended Detection and Response offers a 360° view of documents, identities, endpoints and cloud workloads and reliably detects typical anomalies. It helps protect your IT infrastructure from even the most sophisticated cyber attacks.
When is it the right solution?
Endpoints in companies are the primary target of cybercriminal attacks. As many recent successful attacks have shown, preventative protective measures, such as anti-virus and firewalls, are no longer sufficient. You therefore have to take additional measures to reliably detect and respond to attacks.
The first step
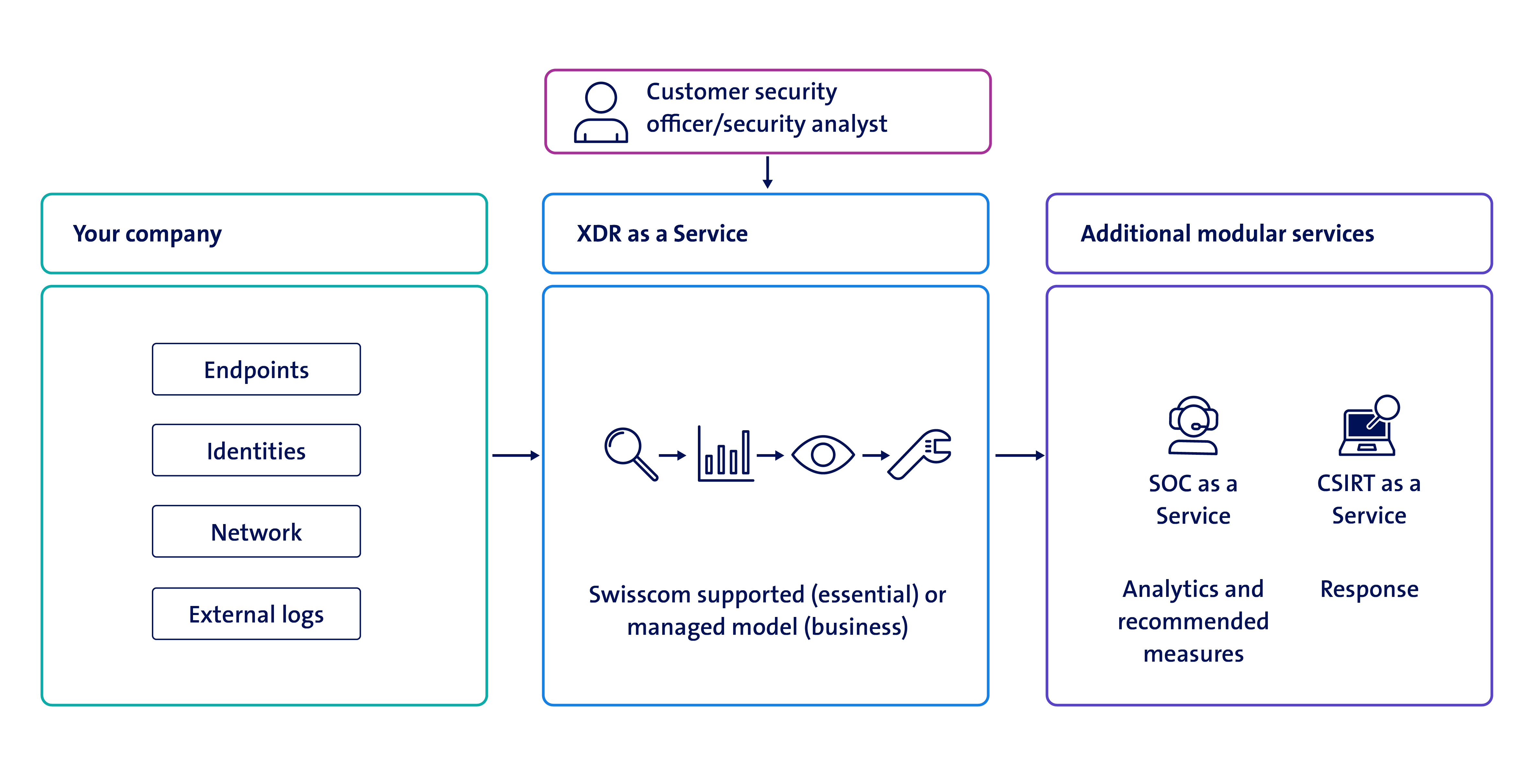
How does Extended Detection and Response (XDR) work?
The service runs on a standardised platform for detecting and responding to security incidents. The platform collects, correlates and evaluates data from multiple security components and sources, including endpoints, identities, apps, e-mails, documents and cloud workloads. Upon detecting unusual behaviour or an attack, the XDR service automatically generates security alerts or incidents. Incidents are centrally visible in the dashboard and can be seen and responded to by the security officers.
Why Swisscom?
Application examples
How Extended Detection and Response supports your security requirements.
Real-time overview
The customer requirement
You want a constant overview of the activities in your IT infrastructure to enable an immediate response to security incidents.
Our solution
The XDR dashboard gives you a real-time, at-a-glance overview of the status of your endpoints and cloud workloads.
Protection against sophisticated cyber attacks
The customer requirement
You want to improve the level of IT security and be protected against sophisticated attacks that circumvent preventive measures such as anti-virus software.
Our solution
Thanks to its behaviour analysis system, XDR instantly identifies suspicious activities on the monitored environments and is able to take action automatically. If manual interventions are also required, your security professionals can respond promptly. XDR increases your level of security.
Protection beyond the corporate network
The customer requirement
Your employees are increasingly working outside your company premises; on site with customers or from home for example. Despite this, smartphones, company laptops, identities, e-mails and documents still need to be protected.
Our solution
XDR is a cloud-based solution that protects endpoints irrespective of how they are connected to the internet. This approach therefore allows the IT strategy to shift from perimeter protection to endpoint security.
A lack of resources to operate XDR
The customer requirement
You want optimum protection for your endpoints, but you don’t have the resources or expertise to operate an XDR solution.
Our solution
Use Extended Detection and Response and the services of a Security Operation Center (SOC) as a Managed Service(opens in new tab) from Swisscom.
Our partner

