To manage IT security incidents effectively, the Security Operation Center (SOC) and the CSIRT need to work hand in glove. While the SOC monitors infrastructure and applications in order to spot security incidents at an early stage (security monitoring, security analytics and security alert handling), the Cyber Security Incident Response Team (CSIRT) is the rapid reaction force, the IT firefighters. This team deals with complex security incidents and initiates threat protection and security incident eradication measures. Together, the two teams make it possible to launch an early response to cyber attacks and to limit any damage.
CSIRT as a Service and Rapid Response
CSIRT Services – your incident response team
It is impossible to prevent serious security incidents 100% of the time.
Which makes it all the more important to act quickly and stop any attacks when such an incident occurs. Complex IT infrastructures and a shortage of IT security specialists make it difficult to create an in-house cybersecurity incident response team (CSIRT), which can compromise cyberdefence.
Calls are free. Call outs are charged at a flat rate plus costs. This offer is exclusively available to companies in Switzerland.
When is it the right solution?
When dealing with a successful cyber attack, business continuity is paramount. You have to guarantee an appropriate incident response whatever your cost pressures or shortage of skills. Outsourcing IT security services could be an option worth considering.
CSIRT as a Service
Services in detail
CSIRT as a Service (CSIRTaaS) involves a prior onboarding process and contract, while Rapid Response is provided as needed, with no contract necessary.
CSIRT as a Service
- 24/7 end-to-end management of security incidents in line with the process defined by Swisscom
- Remote or on-site assistance
- Final report documenting the incident and measures taken
- In-depth analysis and evidence gathering (forensic) for legal proceedings (optional)
- Guaranteed response based on SLA
- Short response times thanks to previous onboarding process
- Costs: Monthly plus per-use billing based on time and materials
CSIRT Rapid Response
- 24/7 end-to-end management of security incidents in line with the process defined by Swisscom
- Remote or on-site assistance
- Final report documenting the incident and measures taken
- In-depth analysis and evidence gathering (forensic) for legal proceedings (optional)
- Best-effort response
- Longer response times than with CSIRTaaS as onboarding is required
- Costs: Flat rate plus per-use billing based on time and materials
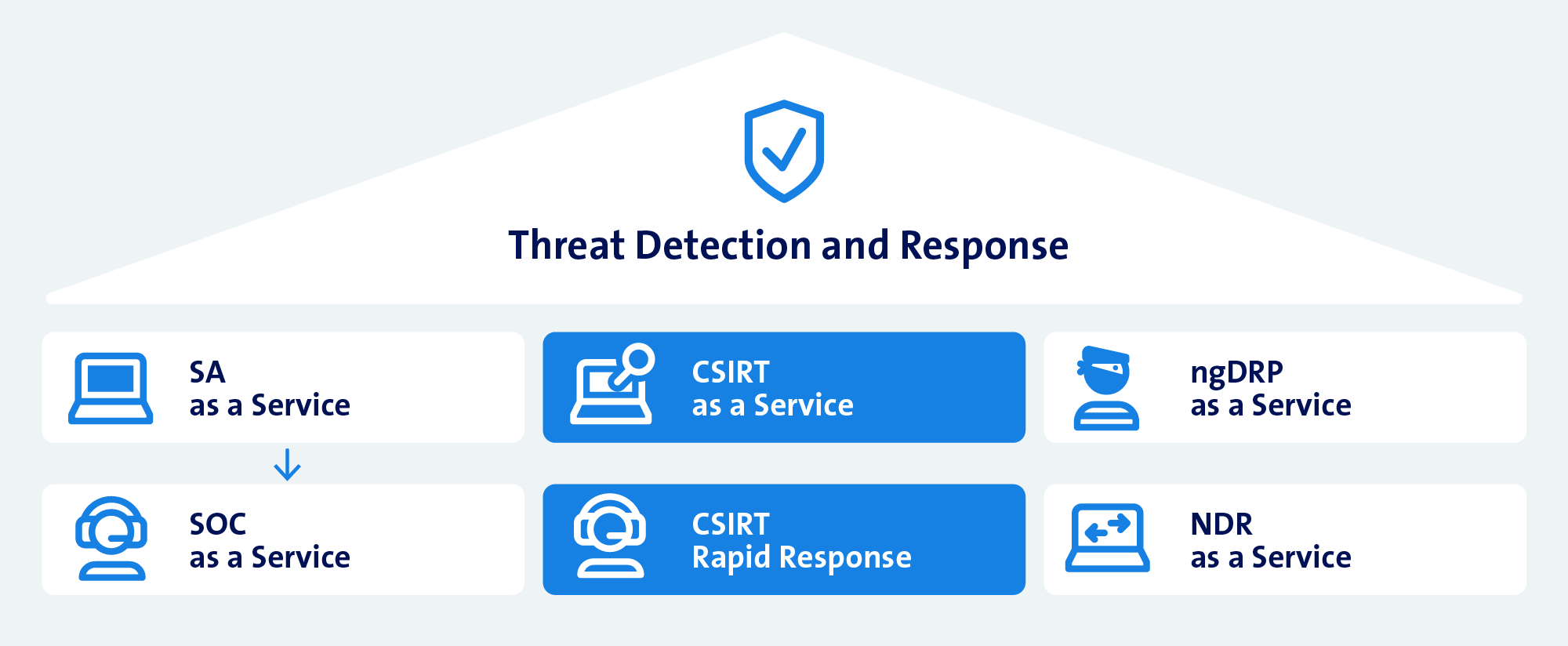
CSIRT as a part of our TDR portfolio
CSIRT as a Service and Rapid Response are a modular extension of the analytical functions of Security Analytics and SOC as a Service.
Why Swisscom?
FAQs: Cyber attacks on Enterprise customers
How does a Cyber Security Incident Response team (CSIRT) respond to incidents?
There is a multi-stage response to incidents. This is generally based on the NIST Incident Management process:
- Identification: Establish an overview of the security incident, determine objective
- Assessment: Analyse incident and recommend emergency measures
- Containment: Secure evidence, classify attack vector, contain the attack
- Eradication: Eradicate the security incident and clean up the systems
- Recovery: Recover normal state, test and monitor system behaviour
- Lessons learned: Debriefing, report and recommended measures
You can find detailed information on this in the CSIRT white paper.
Why is the interaction between the SOC and CSIRT important?
Why should a company consider outsourcing its CSIRT service?
The shortage of specialist staff and the complex, demanding work of a CSIRT make it sensible to consider outsourcing this service. Service providers can guarantee 24/7, end-to-end management of security incidents. Service providers that have cyber security experts with a wealth of experience in dealing with security incidents can guarantee an efficient response to such incidents.
How do CSIRT and CISO/security officers communicate with each other during a cyber security incident?
The type of communication depends on the nature of the incident and the company, and is determined at the start of each incident. If the customer’s infrastructure is compromised, it is advisable to switch to private devices and e-mail accounts, and to do the same with the telephone. Apart from that, the customer’s preferences determine whether communication takes place via e-mail, Microsoft Teams or SwissTrustRoom.