Why many companies are inadequately protected against cyberattacks.
Conventional security architectures today offer company data inadequate protection against unauthorised access. Zero Trust Network Access (ZTNA) shows you how your data can be kept secure in the future.
Text: Egon Steinkasserer and Patrick Strasser, 02 August 2021. 6 min
Fortifications and walls have always played an important role in protecting particular areas. Modern IT security architectures are often based on the same approaches that the Romans followed with Hadrian’s Wall and the Chinese with the Great Wall – seal off areas to control access. However, Greek mythology taught us that even the strongest walls offer no protection against a Trojan horse in the city.
In relation to computer networks, the term “perimeter” to denote the outline; i.e. the border. The architectural concept – perimeter security – is based on the principle that the perimeter is protected against attacks from the outside. All entities (computers, software, people, sensors, etc.) within the perimeter trust each other. Therefore, no special precautions are taken for mutual protection.
Changing threat situation
However, threats now increasingly come from within the perimeter. Individual clients can be infected with malware by attackers; for example, while visiting a website or opening an email attachment. The target of viruses or trojans is typically not the initially infected computer but other more valuable systems, such as database servers or fileservers on the network.
A traditional firewall protects a network only from external threats, like a wall, but cannot protect it against internal attacks. Weak security mechanisms within a perimeter allow attackers to move freely, infiltrate and take control of other computers with extended access rights, and thus penetrate to the company’s most sensitive data. In security jargon, this is referred to as a “lateral movement”.
Eight areas where cyber defence needs to change in order to optimally safeguard the digital transformation.
Changed user behaviour and the public cloud
Company data and applications are increasingly accessed via various devices from outside the company network or anywhere else (on the move or in the home office). In addition, for various reasons (profitability, scalability, etc.), it makes sense for many companies to move applications and data to the public cloud; i.e. outside the traditional perimeter. The need to digitise and simplify interactions and processes with partners and other companies is another driver. In this case, too, the users and systems are outside the company perimeter.
These aspects mean that the traditional network perimeter, and thus perimeter protection, is becoming less important. If the “boundaries" of the company can no longer be defined easily, then the perimeter can no longer be defined and protected clearly.
Changed user behaviour means that data traffic is also shifting. The past was dominated by access to servers and services on the local company network. Access to the internet was the exception. Accordingly, data traffic was divided into 80% local company network (the intranet) and 20% internet. Today, sometimes 90% or more is generated on the internet. Centralising all data traffic via the company headquarters infrastructure in order to control it now makes less sense, since users, data and applications are increasingly located outside the company network (see figure below).
The use of SaaS (Software as a Service) implies that data traffic is decentralised, making it difficult to control. In the past, bandwidth and access speed on a corporate network were almost always better than on the internet. The nationwide provision of broadband internet for all households in Switzerland (at up to 10 Gbit/s) and on the go (with 5G+ up to 2 Gbit/s) is changing this.
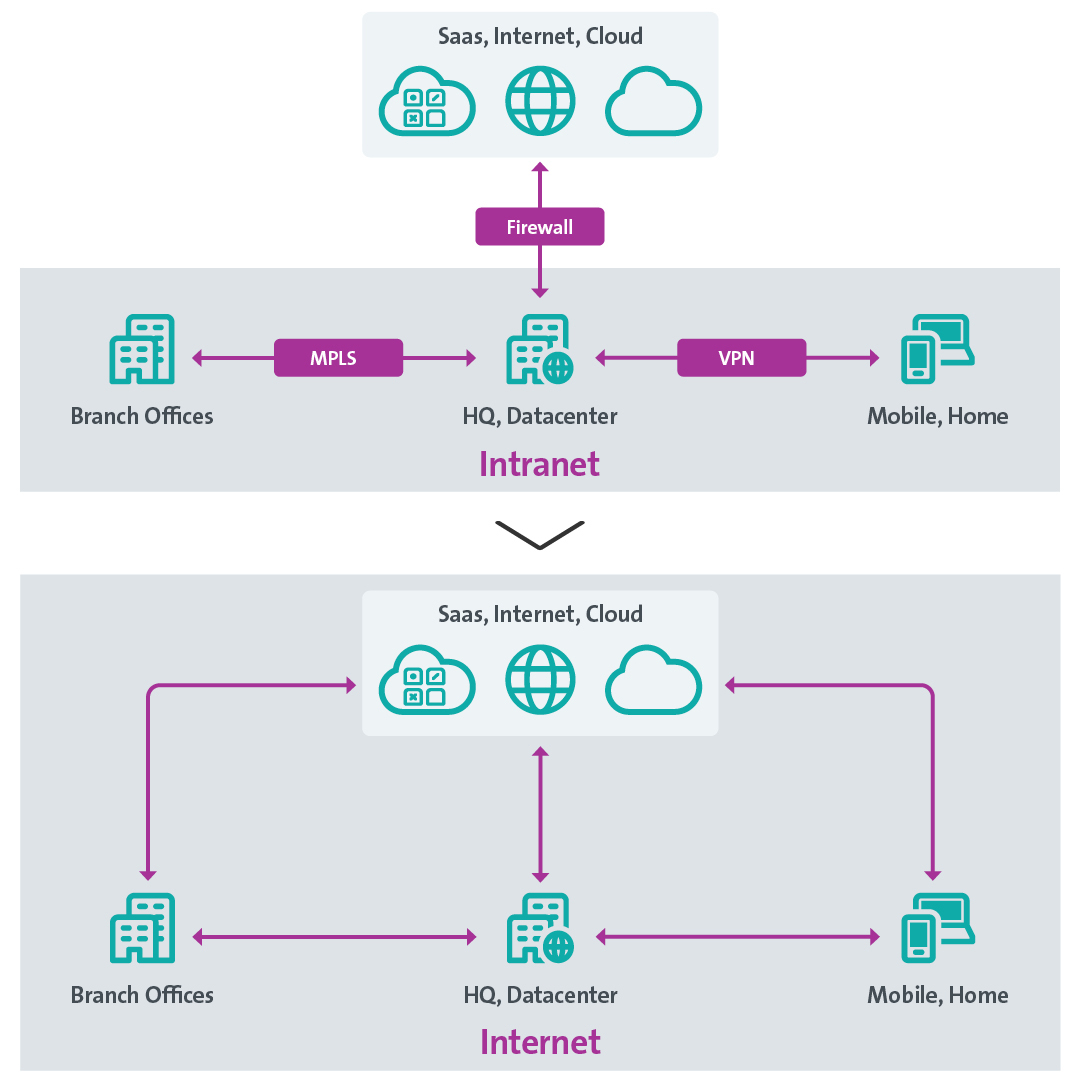
Change in data flows and network architecture (source: Swisscom)
In addition, connections protected with the help of a virtual private network (VPN) often meet current security requirements only to a very limited extent. The goal of end-user VPNs is to establish a secure connection from an end device via an insecure network (internet) to the (supposedly secure) company network. This is ensured on the end device side by installed software (the VPN client), which encrypts data traffic, and on the company side by a corresponding VPN gateway, which decrypts the data again.
Conventional VPNs are based on a perimeter security architecture. The “barn door” to the company network is usually opened completely with the help of an activated VPN, just as if the client were physically located within a company site. Due to the mostly unrestricted access rights of the possibly infected client, attacks can take place barrier-free on many attractive targets in the same network. Unfortunately, to avoid the associated complexity, many installations do not use all the options for restricting access that are available for end-user VPNs.
In addition, VPN solutions often allow only limited transparency on user access. Only connections via the VPN tunnel or internet access at the company location are visible. All other access to SaaS solutions or cloud applications via any internet connection usually remains invisible to the company for performance reasons.
New security concepts are thus necessary to protect the use of data and applications, enable access to company data from anywhere and to meet the current threat situation in cyberspace.

In a crowd of unknown people, there is no mutual (implicit) trust (source: unsplash.com)
Zero Trust Network Access – trust no one
What is the solution if on one hand the perimeter no longer offers sufficient protection, and on the other access no longer occurs via the supposedly secure company network? The answer is – do not trust anyone and verify all connections permanently. This is exactly the principle on which Zero Trust Network Access (ZTNA) is based.
As a comparison, imagine the network as a very busy public street in a city with many unknown people (see Figure above). In this environment, we hand over confidential information only to someone we know beyond doubt, who we expect to meet in this place and whose behaviour we classify as trustworthy. It’s also advisable for the information exchange to take place in such a way that the content is not visible to other uninvolved people. It’s also implicitly clear that only the necessary information is transferred (data minimisation).
ZTNA is based on these same principles:
- All actors and entities in the network are generally regarded as untrustworthy.
- External and internal threats exist at all times.
- The network location is not a sufficient criterion for trust.
- Every device, user and data access must always be authenticated and authorised continuously.
- Access policies must be created dynamically and refer to as many context-specific parameters as possible at the same time (risk-based).
- Only the minimum possible privileges (“least privileges”) are granted to each access in order to minimise the potential for damage in the long term.
- It’s generally assumed that every IT system has security-relevant loopholes and that attackers are omnipresent (“assume breach”).
All devices, accounts or services, regardless of where in the network or in which subnet, are untrustworthy. Every connection between users, services and devices must be authenticated mutually (unambiguous identity) and authorised dynamically (legitimacy and risk profile of the access). Since every network or network element is assumed to be untrustworthy, every type of data traffic must be encrypted, regardless of whether it occurs via a public or a private network. Data access is authorised only for the minimum amount of resources or defined according to privileges. Each access must be checked continuously using the Kipling method(opens in new tab) for who wants access to what, when, from where, why and how.
Compared with perimeter architecture, in which authorisation takes place at the network level for an entire subnet and is based mostly only on IP addresses (and sometimes also MAC addresses), the attack area and the effects of an attack can be reduced dramatically using ZTNA.
ZTNA implies that authentication and authorisation take place constantly. However, this does not mean that users have to authenticate themselves manually all the time. In addition, as much contextual information as possible is included with each access. Examples include:
- device identity
- date and time
- current geolocation of the device (e.g. to restrict legitimate access to certain regions or nations)
- normal user and system behaviour versus anomalies
- device configuration (e.g. it can be checked whether certain security patches have been installed)
- deliberate limitation of the maximum number of simultaneously active users or sessions (throttling)
Access is granted only if all dynamically determined contextual information is within the prescribed parameters. Automatically calculated target parameters can also be compared with the current contextual information with the help of machine learning. This data-centric approach makes it significantly more difficult for attackers to achieve their malicious aims.
Zero Trust Network Access for security and convenience
The limited performance or scalability of conventional end-user VPN solutions mean that employees may have to activate the VPN service selectively, but also deactivate it again (e.g. for video conferences, streaming, access to larger files stored in the cloud). This depends on whether they want to access resources in the company network or on the internet. This is far from beneficial to user-friendliness and productivity, since the establishment of the VPN tunnel is usually associated with a new login, an initialisation phase and thus an interruption to work.
With ZTNA, end-user VPNs largely become a thing of the past, as all connections are encrypted anyway and resources are accessed directly. Secure access to company resources takes place in the background, without user interaction and independent of the location. It’s therefore advisable to gradually replace end-user VPNs with ZTNA and additional technology (e.g. Cloud Access Security Broker, Threat Detection and Response, etc.).
However, ZTNA is much more than just the successor to VPN – not only can communication between users and applications be secured, but also communication between different servers or services (e.g. with identity-based segmentation to enable a Service Mesh(opens in new tab)).
Single sign-on as the basis for improved user experience
Another aspect of security and simplicity concerns access control and administration of access policies. Today, users often have to contend with different logins and authentication methods for different resources (company applications, SaaS solutions, etc.). Centralisation of access control (single sign-on) using directory services, access policies and inventories can greatly enhance the user experience and security. Multifactor authentication (MFA), such as Mobile ID, further increases security and is now a minimum requirement.
Since users rarely have to authenticate themselves again with such solutions, multifactor authentication does not lead to any loss of productivity. Cryptographically secured strong authentication methods can further offer users a consistent experience, regardless of the device or service used.
Increase workplace attractiveness with BYOD and “Multi Device”
Preferences for certain end devices and operating systems are individual. This is shaped increasingly by electronic consumer goods and internet services from the private sphere (the “consumerisation” of IT). Requirements for the form factor, operating system and performance of the device differ markedly depending on the activity. Employees also want to access company data and applications via private devices (bring your own device, BYOD) and use them for their daily work, usually to the benefit of the company. A public computer or a shared device should also be able to be used securely (for the company and employees) if necessary.
Ultimately, it’s about the attractiveness of the workplace and the freedom of employees to choose their way of working according to their preferences – an important factor in competing for the best employees (“War for Talents”).
The conventional approach to workplace management in which only end devices provided by the company can access company data is no longer up to date. The same applies to restriction to a single device. Many knowledge workers would like to be able to use a tablet and a private computer with a large screen in their home office, in addition to a smartphone and notebook (Multi Device).
Any end device can be used with ZTNA in combination with unified endpoint management (UEM) systems. Security requirements are always met, even if the devices are not provided by the IT department or are not or only partially managed by it.i.
All modern operating systems now have sophisticated mechanisms to secure any end device using company-specific security profiles and policies. The company can enforce security settings, requirements and restrictions on the registered devices or delete data from the device remotely (remote wipe). ZTNA includes the end device in the access control. This allows companies to ensure that only devices with certain properties or security settings have access to company resources. It doesn’t matter whether the device belongs to the company or to the employee.
Of course, ZTNA also supports browser-based access. In summary, ZTNA turns a restrictive workplace “trapped” in the traditional perimeter into a flexible and mobile “perimeterless digital workspace”.
Since February 2018, in addition to the traditional workplace, Swisscom has provided all its employees with an optional perimeterless digital workspace developed in the internal “Work Smart NOW Project”. In this flagship project, a zero trust architecture was implemented in order that mobile devices and private computers with many common operating systems and browsers could also be used comprehensively and securely. Currently, about 25,000 devices are registered:
- 11,000 iPhones/iPads with iOS/iPadOS
- 10,000 Android devices (mobile phones/tablets)
- 3,000 Windows devices (PCs/laptops)
- 1,500 Apple Macs with macOS
Summary and recommendations
ZTNA represents a paradigm shift in how access to data and applications is granted. The approach includes mutual authentication of all users, devices and services, control of individual access and behaviour monitoring for anomalies. ZTNA also allows more rapid implementation of IT landscape changes and sustainable improvements to the user experience.

Even the thickest and highest walls are useless if the enemy is already inside the castle (source: Wikipedia)
Although the foundations for zero trust were laid back in 2003 in the Jericho Forum(opens in new tab) and several companies have implemented such large-scale projects successfully since then, adoption is still shockingly low across the board. Too many companies fool themselves with a perceived sense of security while still using outdated best practices.
The dangers of cyberspace are increasing constantly, as shown for example in the current Swisscom Cybersecurity Report(opens in new tab) on the threat situation in Switzerland. Swiss companies are also increasingly affected by ransomware attacks (extortionary trojans), as you can read in the latest MELANI(opens in new tab) half-yearly report from the National Centre for Cybersecurity. The majority of attacks take place indirectly via mobile users or decentralised locations. The National Institute of Standards and Technology (USA)(opens in new tab) has also recognised the need for a new security architecture, which is why the standardisation(opens in new tab) of zero trust was started in order to simplify use of the new capability.
The security guidelines for products and services that have been in force at Swisscom for many years take into account and promote the basic principles of ZTNA. We recommend that all companies become familiar with modern security concepts, in particular the topic of zero trust. In a first step, all user access to systems or company resources, which usually represent the greatest risk, should be secured with ZTNA (and MFA). In a second step, access between systems and services should be protected according to zero trust principles. In many cases, costs can also be reduced since manual administration of often thousands of firewall rules is no longer necessary and network complexity can be reduced massively.
Let’s look back at history and specifically at Greece. The millennia-old knowledge from Homer’s Iliad (the Trojan War) can now also be implemented in network security. Even the thickest and tallest walls are useless if the enemy is already inside the castle – trust no one and check everyone!
