Innanzitutto, è necessario spiegare brevemente la differenza tra "accesso programmatico" e "accesso alla console di gestione". L'accesso programmatico viene utilizzato quando un utente o una macchina ha bisogno di accedere all'interfaccia a riga di comando (CLI) di AWS, agli SDK di AWS o alle chiamate HTTPS dirette alle API dei singoli servizi AWS. Strumenti come Ansible o Terraform sono esempi tipici di questo tipo di accesso.
Poi c'è l'accesso alla console di gestione. Normalmente, un essere umano accede alla console di gestione tramite un browser web. L'utente si autentica con un nome utente e una password (e auspicabilmente con un secondo fattore) per accedere all'interfaccia grafica per la gestione delle risorse.
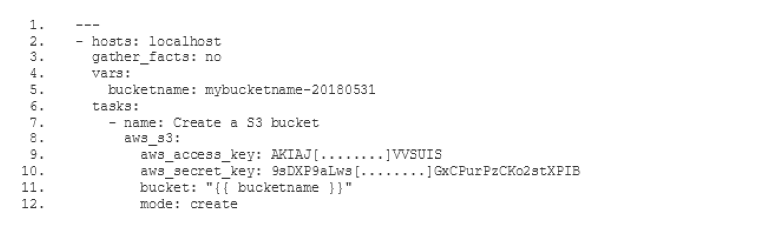
D'ora in poi questo articolo si concentrerà solo sull'accesso programmatico. I dati di accesso per l'accesso programmatico sono chiamati chiavi di accesso. Le chiavi di accesso sono costituite da due componenti: un ID della chiave di accesso e una chiave di accesso segreta. Potrebbero avere il seguente aspetto: