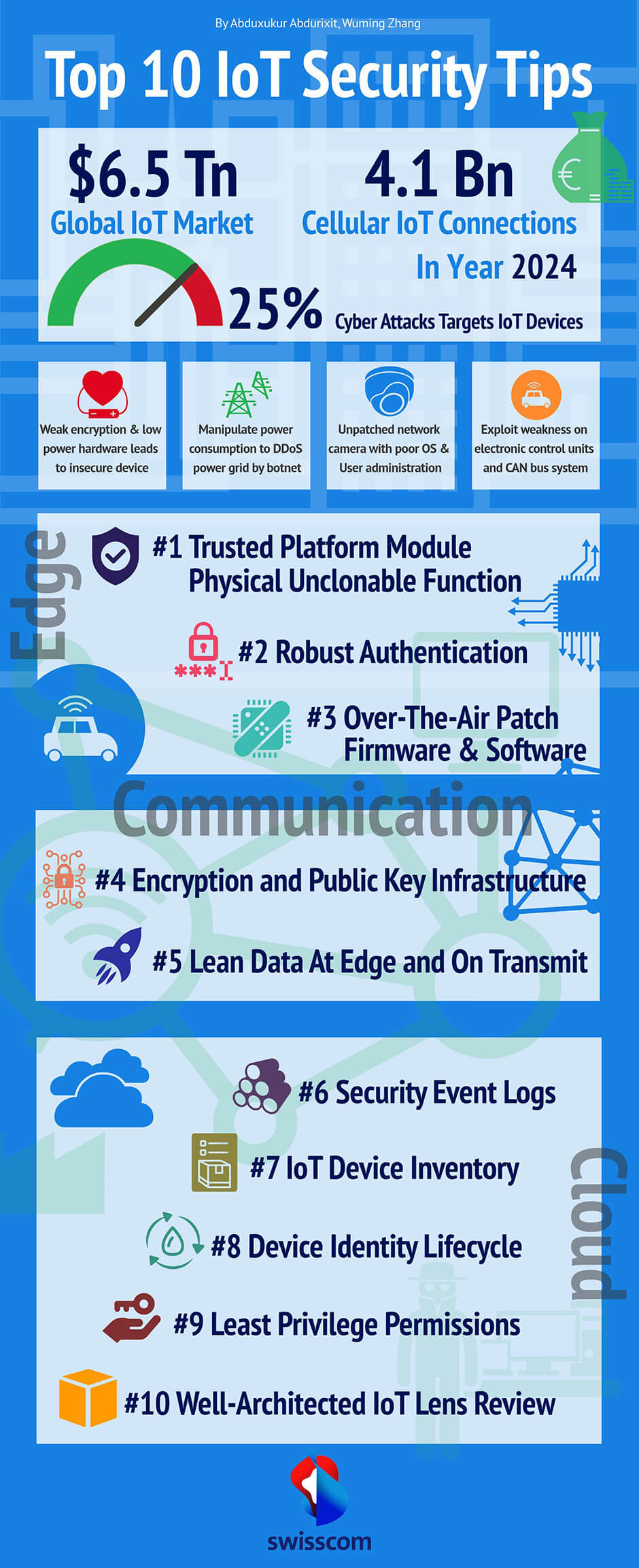
A parte questo, a prescindere dall'hardware. Usa un modulo di piattaforma affidabile o una funzione fisicamente sbloccabile per proteggere fisicamente il dispositivo dalla manomissione. Un'autenticazione locale forte per evitare che il dispositivo venga violato con la forza bruta. Il software è intrinsecamente pieno di bug, quindi gli aggiornamenti over-the-air o una sorta di gestione delle patch sono essenziali.
Quando comunichiamo, dobbiamo garantire la crittografia dei dati a riposo e di quelli in transito. È indispensabile lavorare con i certificati digitali. Utilizzare metodi di difesa aggiuntivi a livello di rete per rilevare il traffico insolito. Se snelliamo i dati ai margini della rete, è difficile che terze parti non autorizzate riescano a capire i dati. Consegnare i dati non appena arrivano nel cloud.
Nel cloud, dobbiamo raccogliere tutti gli eventi relativi alla sicurezza dai dispositivi edge e impostare un sistema di allarme come controllo investigativo. Un corretto inventario dei dispositivi IoT con il ciclo di vita dell'identità ci aiuta a evitare che il dispositivo finisca nelle mani sbagliate. Il privilegio minimo per ogni dispositivo e utente è fondamentale per evitare errori di configurazione. Infine, ma non meno importante, una revisione continua e ben ponderata dell'intero sistema con IoT Lens è sempre preziosa e necessaria per scoprire, misurare e migliorare la sicurezza e le prestazioni generali dell'IoT.
Entro il 2024, il 25% dei dati che generiamo sarà disponibile in tempo reale, il che significa che dobbiamo garantire la sicurezza fin dall'inizio. Si tratta di un compito impegnativo che riguarda tutte le aree aziendali. Seguendo le migliori pratiche di sicurezza e i nostri dieci consigli per la sicurezza dell'IoT, possiamo tracciare una strategia generale di cybersicurezza dell'IoT e implementare misure di sicurezza in tutta l'organizzazione. Non importa quanto siano estese!