The Swisscom Application Cloud uses the open-source distribution of Cloud Foundry as it’s basis to provide you with a platform-as-a-service.Ever since our platforms official release we’ve continually been adding and implementing new features, and one of these is the Container-to-Container Networking.
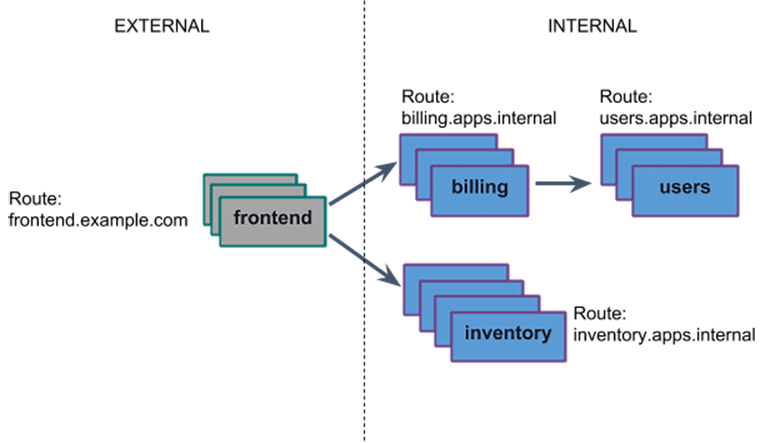
Container networking enables a policy-driven, direct communication between your application instances on Cloud Foundry.
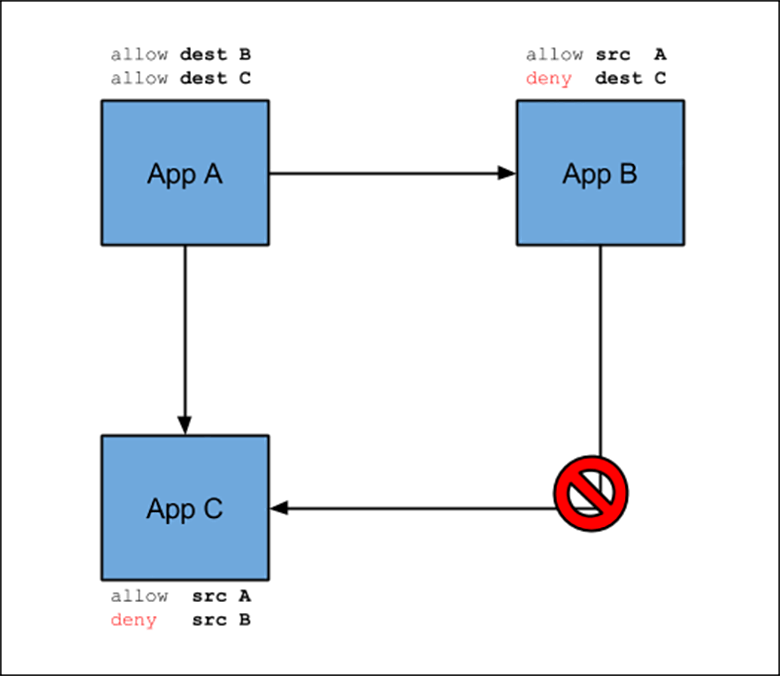
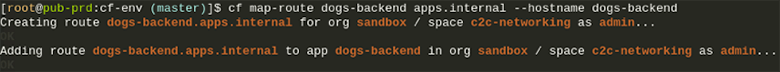
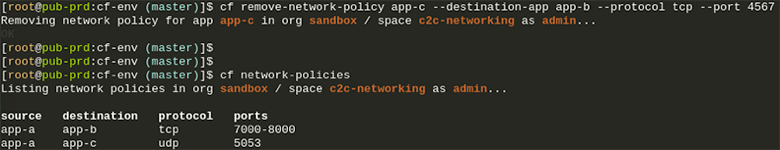
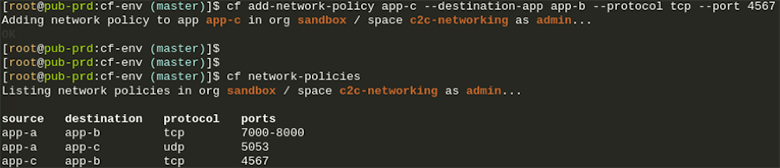
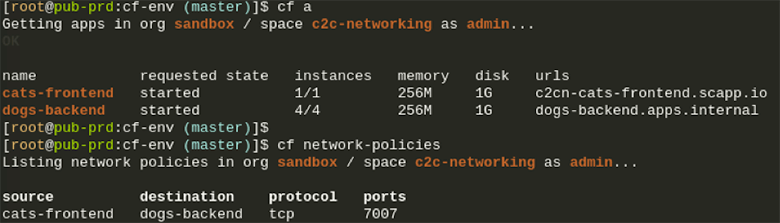
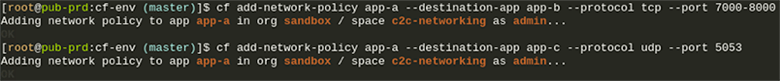
Based on policies you can set through the CF CLI, your applications now have direct connectivity with each other, either through TCP or UDP. Your choice!This of course provides many benefits like reduced latency and increased throughput thanks to direct communication instead of going through the GoRouter or an external load-balancer. It also enables you as a developer to set fine grained access controls through these app to app policies. Your apps become more secure with private communication between each other directly, using the container IPs instead of having to use a public route. This also gives you the option to hide applications from the outside and access them without adding a route to them.
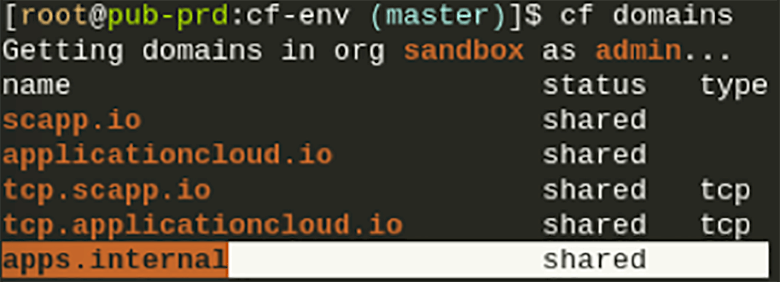
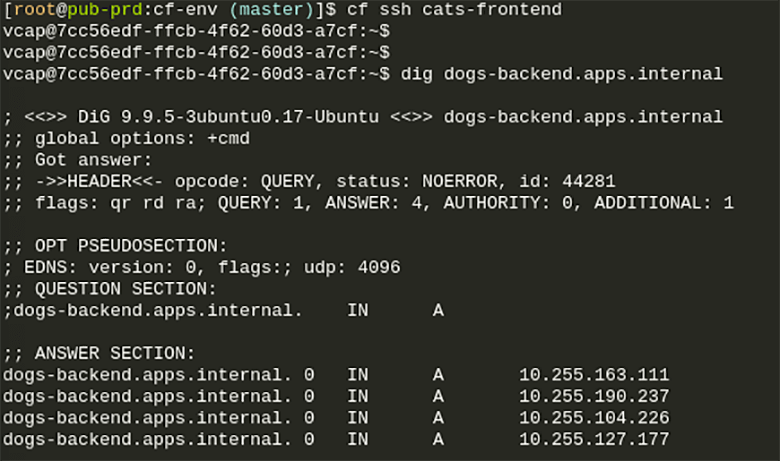
Container-to-Container Networking internally uses an overlay network to manage and allow communication between your app instances. All app containers are assigned a unique private container IP address, which they then can use to talk to each other.The overlay network is not externally routable, and traffic sent between your containers does not exit the overlay network.
You can get an in-depth look at the architecture behind the scenes here on GitHub: https://github.com/cloudfoundry/cf-networking-release/blob/develop/docs/arch.md(opens in new tab)