Cloud
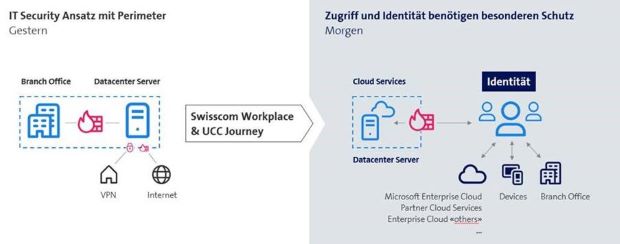
Cloud security: from perimeter protection to identity-based security
It's not just the way we work that is changing rapidly, but also the way we handle data and where it is stored. New technologies are increasingly influencing our working and private lives. Smart devices (smartphones, tablets, smartwatches) are now established work tools and are widely used. The younger generation can no longer be attracted to a company without flexible working models. The need to be able to access and share applications, information and data at any time using various devices is growing dramatically. In addition, more and more companies are taking their first steps into the cloud (e.g. outsourcing the email server to Office 365) without adapting their security concepts. Traditional security concepts are being pushed to their limits by all these trends.