Account details, credit card details and access to the company’s network: phishing e-mails are how such confidential information gets into the hands of cybercriminals. These tips will help you recognise phishing e-mails and protect yourself and your SME.
Seventy to 90 percent of all cyberattacks start with phishing e-mails, which open the door for the attacker to access a company’s network or a business’s online account. Once the door is open, the cybercriminals start wreaking havoc. They try to scam money or encrypt all company data with ransomware in order to (perhaps) release it again in exchange for a ransom.
The problem is that phishing e-mails are incredibly versatile, making them difficult to detect and block with technical protective measures. It takes you as a human being to use your common sense to recognise – and stop – such attacks.
What are phishing e-mails?
Don’t give cybercriminals a chance!

The short e-learning session provides three basic conduct tips for employees, such as how to protect themselves against phishing and how to create secure passwords, and thus help to improve security in the company.
Phishing is a scam tactic used by cybercriminals. In a message sent by e-mail, SMS or phone, they assume a false sender identity – usually that of a well-known company – to lure recipients to fraudulent websites or induce them to open an attached document containing malware.
To increase the impact of these e-mails, cybercriminals use psychological tricks known as social engineering: they feign authority (using a known company as the sender), put recipients under time pressure with short deadlines or an allegedly limited offer or scare them (‘act now or your account will be deleted’).
The sophistication of phishing e-mails varies. At the lower end of the scale are e-mails in English with numerous spelling errors that are said to have originated from a Swiss company. On the other hand, it is harder to identify e-mails sent in response to existing communication. The following tips will help you unmask phishing e-mails and thwart cybercriminals’ intentions.
How to recognise phishing e-mails
Here are the most important general ways to identify fraudulent emails and the tips for dealing with them securely:
- Cryptic e-mail address: A spaghetti of letters and a domain (the part after the @ sign) that doesn’t match the pretended sender are a clear sign. But be careful: it’s easy to fake sender addresses. This means that phishing e-mails can also come from a seemingly legitimate sender or even from the real address of a stolen e-mail account.
- Call to take immediate action: For example, if you need to activate your credit card immediately or check a confirmation of receipt, it might just be a psychological trick on the part of a cybercriminal. We humans tend to make more mistakes when we’re under stress – for example, clicking on a phishing link.
- You are not a customer at all: If you receive a letter from a financial institution with which you are not a customer, it is a phishing e-mail.
- Link text and link do not match: The text in the e-mail shows a trustworthy address such as www.swisscom.ch, but the link takes you to a completely different page. This is a classic cybercriminal trick. Many phishing sites hide behind a legitimate address on a hacked server. Or, the scammers use a URL shortening service like ‘t.ly’, which redirects to the actual destination. An address like ‘https://t.ly/something’ may be a sign of attempted fraud, but it does not have to be.
You can see the destination of a link in an e-mail if you hover the mouse over the link – without clicking!
- A lock in your browser does not automatically it is mean trustworthy: with secure connections (https:), browsers show a padlock to the left of the address. But even cybercriminals now use secure addresses to avoid being noticed. Insecure links (http:) in phishing e-mails are a thing of the past.
- Spelling mistakes and simple language: Poor German or English – or both – and simple language are hallmarks of a phishing e-mail. However, don’t draw the inverse conclusion that an error-free e-mail is legitimate.
- Impersonal form of address: Addresses such as ‘Hello’, ‘andiheer’ (the first part of my e-mail address) or no salutation at all point to a phishing e-mail. The reason being that the attacker does not know your real name. However, this does not apply to targeted attacks.
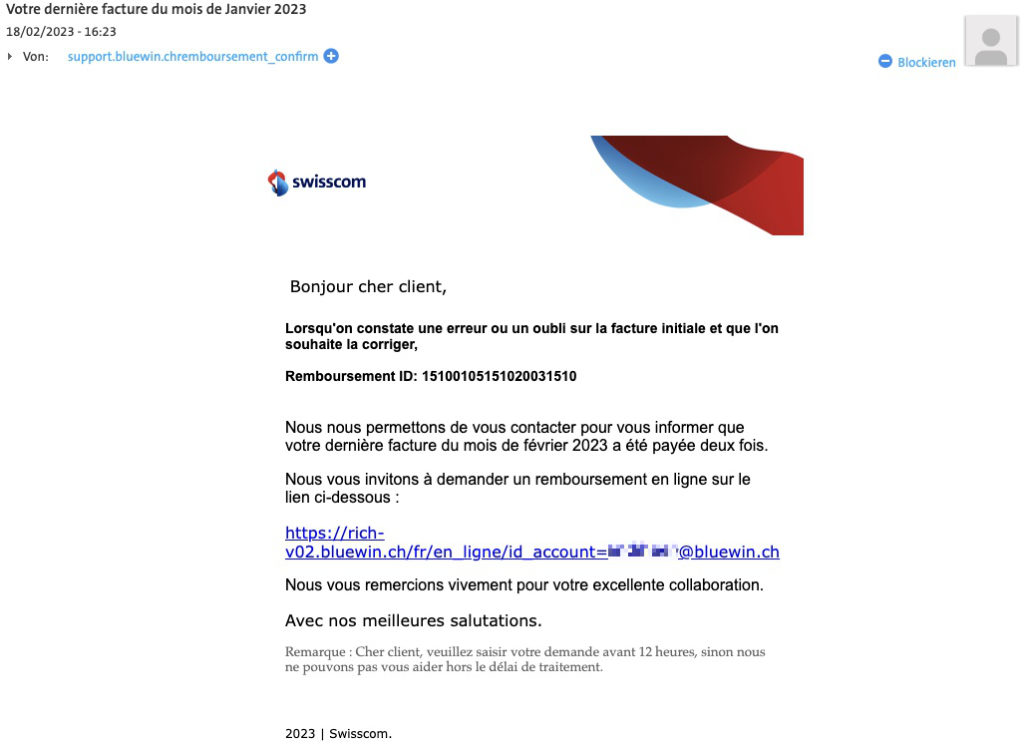
- Suspicious attachments: In the case of invoices or a delivery confirmation as a Word document or an attached unsolicited application as a PDF, caution should be exercised, especially if the file name is very generic (‘application.pdf’). Although Microsoft has prevented the execution of potentially dangerous macros in downloaded Office documents, attackers simply resort to other file formats. The PDF in the phishing e-mail shown below contains an e-mail address (you guessed it, a cybercriminal’s account). If you contact them, the attackers will try to get hold of your personal data or your money.
If in doubt, ask the (alleged) sender. but not by replying to the e-mail. You can do so by visiting the company’s website and searching for their contact information.
- Disclosure of personal data: Does the sender want you to reply to the e-mail with personal data? Then it is almost guaranteed to be a phishing e-mail, for example in the case of fake lottery wins and competitions. Your bank or any other online service provider will never ask for your password. Such requests are another indicator. It is more unclear if you are directed to a login page.
In case of doubt, do not click on the link. Instead, open your browser and enter the address of the (alleged) sender. - Fake login windows for online services: one clever scam is to mimic the sign-in window of cloud accounts such as Microsoft 365 or Google. The trick behind it: you will be prompted to log in – supposedly to open a protected, confidential document. The deceptively real-looking login screen with what appears to be a correct URL delivers your account details straight to the cybercriminals.
Try using the mouse to drag the login window over the edge of the browser window behind it. If this does not work, it is probably not a real browser window, but an attempted attack.
Increase your vigilance against phishing
Well-informed employees are the key to improving IT security in your SME. Security awareness training promotes knowledge and security awareness.
What to do with phishing e-mails?
If you have determined that an e-mail is fraudulent, or at least suspect it to be, you can forward it to these two places, which will help reduce the number of phishing e-mails that reach inboxes:
- Your e-mail account provider: the address is often ‘abuse@’ or ‘spam@’ and the domain of the provider, e.g. spamreport@bluewin.ch.
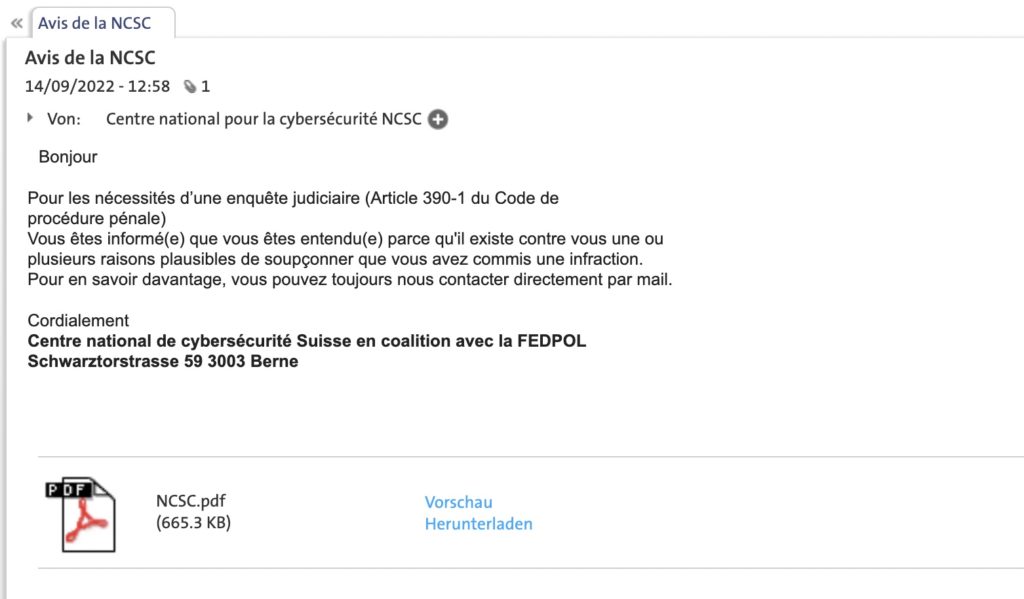
- Reporting address of the federal government’s National Cyber Security Centre (NCSC).
If your work computer or business smartphone is affected, report the incident to the responsible person immediately.
If possible, forward the original e-mail as an attachment. This ensures that all the information about the original sender is retained. Then delete the e-mail in order to not fall for the bait.
Revised version of an existing article.

